Cybersecurity
is a mess
“Wisdom is the principal thing; therefore get wisdom: and with all thy getting get understanding.” ~ Proverbs 4:7
You know that guy Mike Rowe who does that show “Dirty Jobs?” You might think of the old saying, “It’s a dirty job but someone has to do it.” Thus, when I say, as in the title of this essay, that Cybersecurity is a mess, that is simply factual, not meant as admonishment. It is a big business, running into three hundred billion dollars in annual sales this year, industry wide.
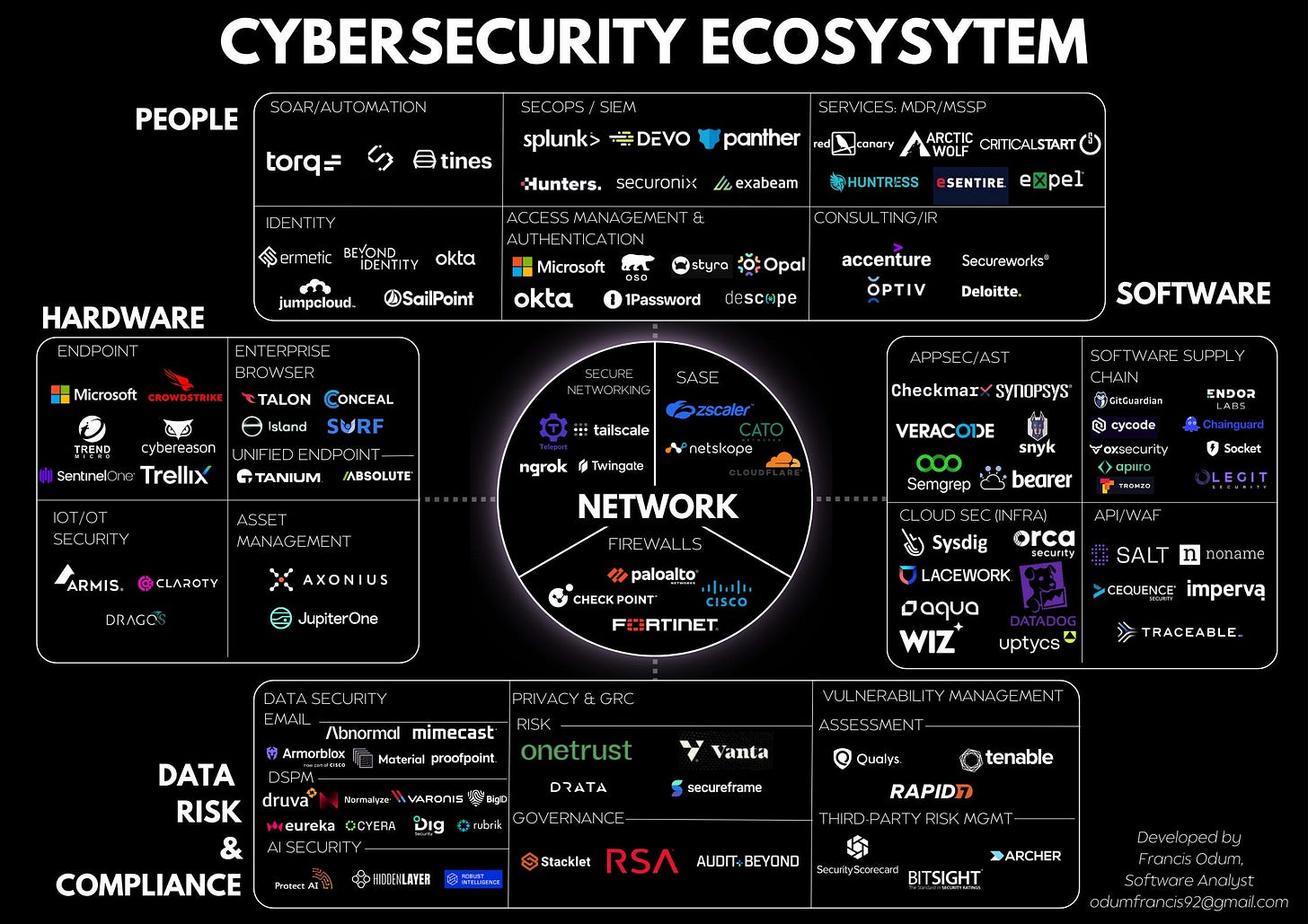
As you can see from Francis Odum’s graphic at the top of this essay, there are about twenty-three definable subsectors to this industry. I’ve chosen to start a new venture in communications privacy and data security education. You can see from the graphic above that there are several vendors in each of those subsectors. You don’t see all the vendors, and let me assure you that there are dozens more. Yes, there is some overlap from companies that are engaged in services for more than one sector. No, there is no really effective cybersecurity “solution” for individuals nor one basic answer for what to do for a small business, let alone a very large one.
So when I say “cybersecurity is a mess” I mean that it is full of answers, some of which are good, many of which are mediocre, a few of which are bad, and it is full of vulnerabilities, limitations, penetration testers wearing all colours of hats, good actors, bad actors, miscreants, ruffians, regulators, and agencies hither and yon. From my perspective starting a new cybersecurity teaching enterprise, that’s not a bad thing. It has the aspects of “job security” in that there will always be lots of students wanting to understand the topic and navigate the mess.
Please note that the new venture I’m building intends to put together a list of elements to our own solution for the individual user and for the small business owner. Please do not view any of the entries on the graphic above as being in any way endorsed by me or by the new enterprise. In some cases, be advised that I am definitely not in agreement with them.
Avoid these
I’ve spent a lot of years in the computer field. I’ve done a lot of programming, including an integrated healthcare practice management database app for which I did all the coding, all the implementation, bug fixes, on-the-fly management, and which was successful in managing data on hundreds of patients for dozens of law firms involving eight doctors, twenty nurses, and recovering tens of millions in fees for patients, law firms, and the medical practice during five calendar quarters of development and operation. I’ve worked on a diverse array of hardware platforms, communications systems, with any number of software vendors, with manufacturers of hardware, with avionics and launch systems designed for intense acceleration and vibration environments, and with an assortment of experts.
I do not trust and would not work with Palantir, Microsoft, Google, Facebook, Twitter, and related software systems and enterprises except as needed to help a client get out of difficulty, or in the event of other extenuating circumstances. By the same token, and for entirely the exact same reasons, I do not work with any of the espionage agencies for whom all the business entities named in this paragraph are contractors. These are not the good guys. These are “tech bros” and technologists who seek to subvert human freedom, destroy decency, create disharmony, and fill data systems with mountains of purloined and ill-gotten information on everyone on Earth for nefarious purposes.
A century ago they would have been described as functionalists. Lately they are referred to as technologists. Before the functional revolutionaries began spewing their venomous diatribes the concept was “managerialism” and the managed society promoters were some of the most authoritarian jerks you can imagine. Yes I would refer you to the 1877 words of Cecil Rhodes, extended and amplified in his subsequent writings in which he called for freemasons to establish a secret society to subjugate all of the world under the British empire. Since he then went about gathering up gold and diamond and other precious metals enterprises in Cape province, in South Africa, in Rhodesia, and elsewhere, and since his wealth was turned to putting together the Rhodes scholarships that brought Hillary and Bill together, funded things like Chatham house, Tavistock institute, the council on foreign relations, and many other “Progressive” enterprises, I think it is useful to continue to finger him as the progenitor of whole new levels of evil which have been hurting billions of people in the last 150 years.
You are, of course, free to choose for yourself. My beliefs do not require that you share my beliefs. If you feel that I should be more persuasive, feel free to let me know in the comments and I’ll do what seems best to reply. Some replies may take longer than others.
More to come
None of the companies that I’ve looked at with respect to cybersecurity have as much as 10% of any of the subsectors. Each of those activities is what business school professors call “highly fragmented.” That means that there are many providers none of which has dominant market share.
Obviously that’s an opportunity for growth by acquisition. Buy market share by buying several companies in a given subsector. Vertically integrate by buying companies in related subsectors. Provide a complete solution that has significant market share (ten to fifteen percent) with the intention of growing the market for cybersecurity while at the same time growing the company to have twenty to forty percent market share. Entrepreneurship professors use the term “roll up” to describe this strategy. Doing so would make it easier to understand the industry and easier to teach what needs to be taught to make use of the technologies.
Meanwhile there is a lot of research and studying to be done. So:
That’s all I’ve got for today. Come back next time when I have something new. Or old.


A little short.
But, we're of the same mind.
Rhodes had his backers...
I don't trust any of their scholars either.
Old chattel "Slavery" mostly ended but the slavers didn't go away. They're still amongst us scheming, plotting, building new forms of human capture, control and exploitation.
Cheers!
When I was working in the energy generation sector, there was a lot of data and security "upgrades" going on. During one meeting on a project in 2010 I chimed in, Where's this gear made? Someone answered, China. I knew the answer but just wanted to hear the engineer say it. Did the head of IT object or show any concern? Nope. I offered that maybe we shouldn't be putting Chinese gear near our nuclear reactors. There was no agreement, only a sigh and eye roll from the team as they wanted the meeting over and to get on to lunch.
Cybersecurity was an afterthought.
The attitude was- get the gear in and we'll plug any holes found later.
Terrifying.
My belief is that the "vulnerabilities" that didn't previously exist were being intentionally installed. IMHO.